Computer Infrastructure has become the repository for storing confidential information. Cryptology is the most efficient way to keep information from unauthorized access. NATEK GUARDIAN is a solution to encrypt the data and share encrypted data between users. Easy installation and management is a distinctive feature of NATEK GUARDIAN.
Information security is becoming more important for all organizations as their dependency on IT infrastructure is increasing. Possible leakage of information can result in big damages and result in a loss of creditability for many organizations. Encrypting information is one of the most common ways for protecting information.
NATEK GUARDIAN is developed to satisfy the data protection requirements for organizations offering an integrated platform for file and mail encryption based on user and user groups.
Structural Features
NATEK Guardian offers complete encryption platform for corporations.
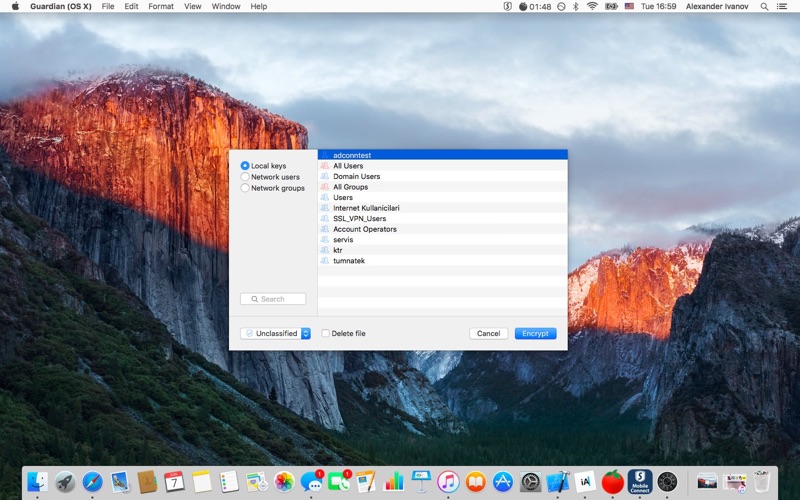
The special key generated for user and any user groups makes it possible to encrypt the data. The key generated uses RSA encryption algorithm.
Data encryption can be performed for files, folders and e-mail messages.
Encrypted files are decrypted automatically if the user has the permission to use generated encryption keys. The decryption is transparent to the user.
A specially designed auditing infrastructure enables central detection of all encryption and decryption activities.
Department administrators can manage their assigned user groups for which they are responsible.
Usage of USB tokens for authentication offers a more secure mechanism for organizations requiring additional security.
A unique password reset mechanism is offered where only special users can reset passwords. A workflow for resetting passwords can be created for multiple approvals.
Main Features
Offers a simple and manageable approach for data protection and encryption requirements.
Possibility of encrypting all data on Windows based client and servers.
Centralized auditing.
Easy deployment and simple usage.
Not dependent on PKI infrastructure.
Encrypted data can be shared between users.
Users can determine password reset workflows for multiple approvals.
System Administrators are controlled and do not have the privilege to control password management for defined users.
USB token support.
End users can create groups for which the system administrator cannot change memberships.
Strong key protection.
File/Folder and e-mail encryption.